Thread by professional hog groomer
- Tweet
- Jan 26, 2023
- #Cryptocurrency #Politics
Thread
In 2009, Bitcoin appeared seemingly out of nowhere and quickly swept across the globe.
But what if Bitcoin’s roots extend back over 80 years prior, to the origins of the US security state?
This is the story of Bitcoin, the NSA, and Crypto AG 🧵
But what if Bitcoin’s roots extend back over 80 years prior, to the origins of the US security state?
This is the story of Bitcoin, the NSA, and Crypto AG 🧵
Born in 1892, Boris Caesar Wilhelm Hagelin was the son of a wealthy Swedish oil baron who worked for the Nobel family in Azerbaijan. In 1917, when the Red Army moved into Baku and the Bolsheviks seized power, Hagelin’s family fled to Sweden.
In 1925, Hagelin was entrusted by Emanuel Nobel with supervising a small Swedish company called A.B. Cryptograph, a designer and manufacturer of ciphering machines.
It wasn’t long before Hagelin appeared on the radar of the chief cryptanalyst for the US War Department, William F. Friedman, who later led the Signals Intelligence Service (proto-NSA) for a quarter century.
The US Army tasked Friedman with evaluating foreign cryptographic machines for possible use. In 1927, Friedman became acquainted with Hagelin’s company and they quickly became friends, bonding over their shared Russian heritage and passion for cryptography.
In May 1940, Hagelin traveled on the last ship from Europe to the US, with two prototypes in his luggage. This trip culminated in the largest ever sale of C Machines, selling his patent rights to the Americans. By the end of the war, the US had produced over 140,000 units.
But how did they work?
The advent of modern cryptography began with the invention of rotor-based cipher machines. Much like the well-known Enigma machines, early Crypto AG machines featured electro-mechanical rotors used to encode plaintext communications.
The advent of modern cryptography began with the invention of rotor-based cipher machines. Much like the well-known Enigma machines, early Crypto AG machines featured electro-mechanical rotors used to encode plaintext communications.
Rather than swapping one letter for another, which would be trivial to crack, rotor machines replace letters in a message with a different letter each instance as the rotors advance, with the device continuously creating new pathways during the message encryption.
Encrypting with these machines required the use of key sheets—strict configuration schedules exchanged by communicating parties ahead of time—laying out the exact machine settings (amongst billions) to be used that day during encrypted communication.
www.youtube.com/watch?v=V6ev1xL1TPs
www.youtube.com/watch?v=V6ev1xL1TPs
After WW2, Hagelin returned to Sweden. But the Swedish government considered ciphering machines war materials, and so to avoid government interference, Hagelin moved his operations to Switzerland.
There, in 1952 with just one employee, he founded Crypto AG.
There, in 1952 with just one employee, he founded Crypto AG.
Hagelin and Friedman stayed in contact after the war as the demand for ciphered telegraph transmission accelerated. Crypto AG was at the time the only civilian manufacturer of cipher machines in the world, and so Hagelin got to work providing updated versions of its machines.
However, the CIA deemed this expanding market for Hagelin’s machines a security threat, worrying unbreakable cryptographic machines would be sold to the USSR. Conversely, the CIA also saw potential in using the machines to gather intelligence from the USSR and its satellites.
Friedman discerned a way to accomplish both.
In 1953, he began by persuading Hagelin to restrict sales of secure machines to pre-approved countries. Initially, the operation was merely a “Gentleman's Agreement” between the two friends.
In 1953, he began by persuading Hagelin to restrict sales of secure machines to pre-approved countries. Initially, the operation was merely a “Gentleman's Agreement” between the two friends.
Then, in 1955, the NSA formalized the agreement with Hagelin: Crypto AG would continue supplying the NSA with information on its customers, supply backdoored machines to countries targeted by the CIA, and supply NATO countries with secure machines.
But how was the NSA able to read the supposedly encrypted messages?
One of the most direct ways was through machines modified to transmit the random encryption key automatically and discretely alongside the enciphered message.
One of the most direct ways was through machines modified to transmit the random encryption key automatically and discretely alongside the enciphered message.
The NSA also secretly helped to write Crypto AG’s user manuals, which ostensibly provided guidelines for the “proper” use of the machine. In reality, these guidelines configured the devices to produce a short ‘cycle time’, which was then easily cracked by the NSA.
As technology advanced, the state-of-the-art cryptography machines progressed in parallel, from mechanical to electro-mechanical to electronic. By the mid-1960s, most machines had begun incorporating recently invented integrated circuits, aka “crypto hearts.”
When Friedman died in November 1969, US intelligence quickly set plans into motion. Within six months, the CIA and the BND (Germany’s foreign intelligence agency) had purchased Crypto AG from Hagelin as part of a secret operation codenamed THESAURUS, and later RUBICON.
Hagelin’s son, Bo Hagelin Jr, had been vocally against the deal with the CIA and the BND, arguing against the sale of compromised machines. But a mere five months after the deal went through, Bo was killed in a car crash. The then VP of the BND believed he was murdered.
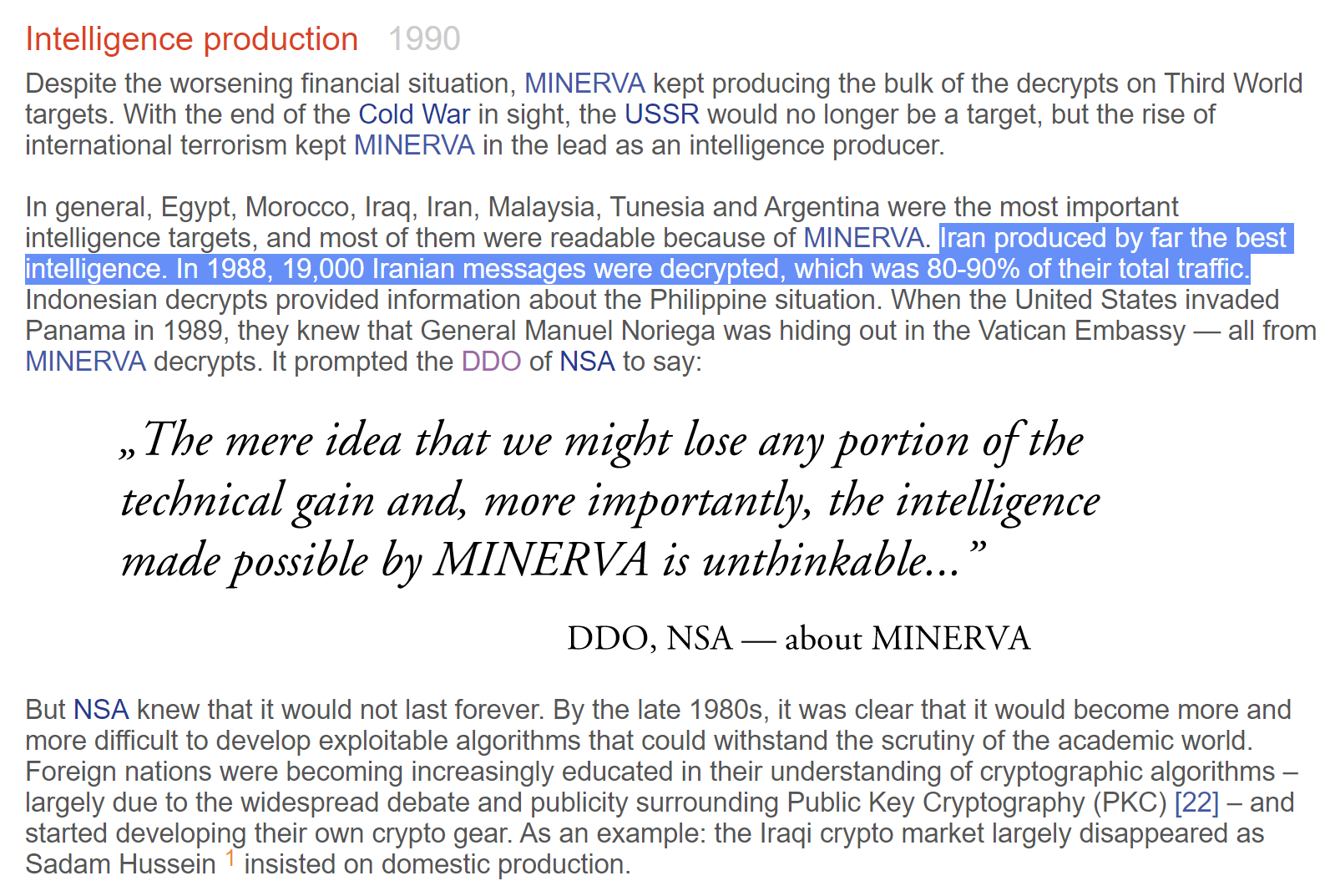
After the change in ownership, Crypto AG was codenamed ‘Minerva’ for the Roman goddess of strategic war. From 1970 onward, the CIA and BND were presiding over virtually every facet of Crypto AG’s operations, all the way down to hiring decisions.
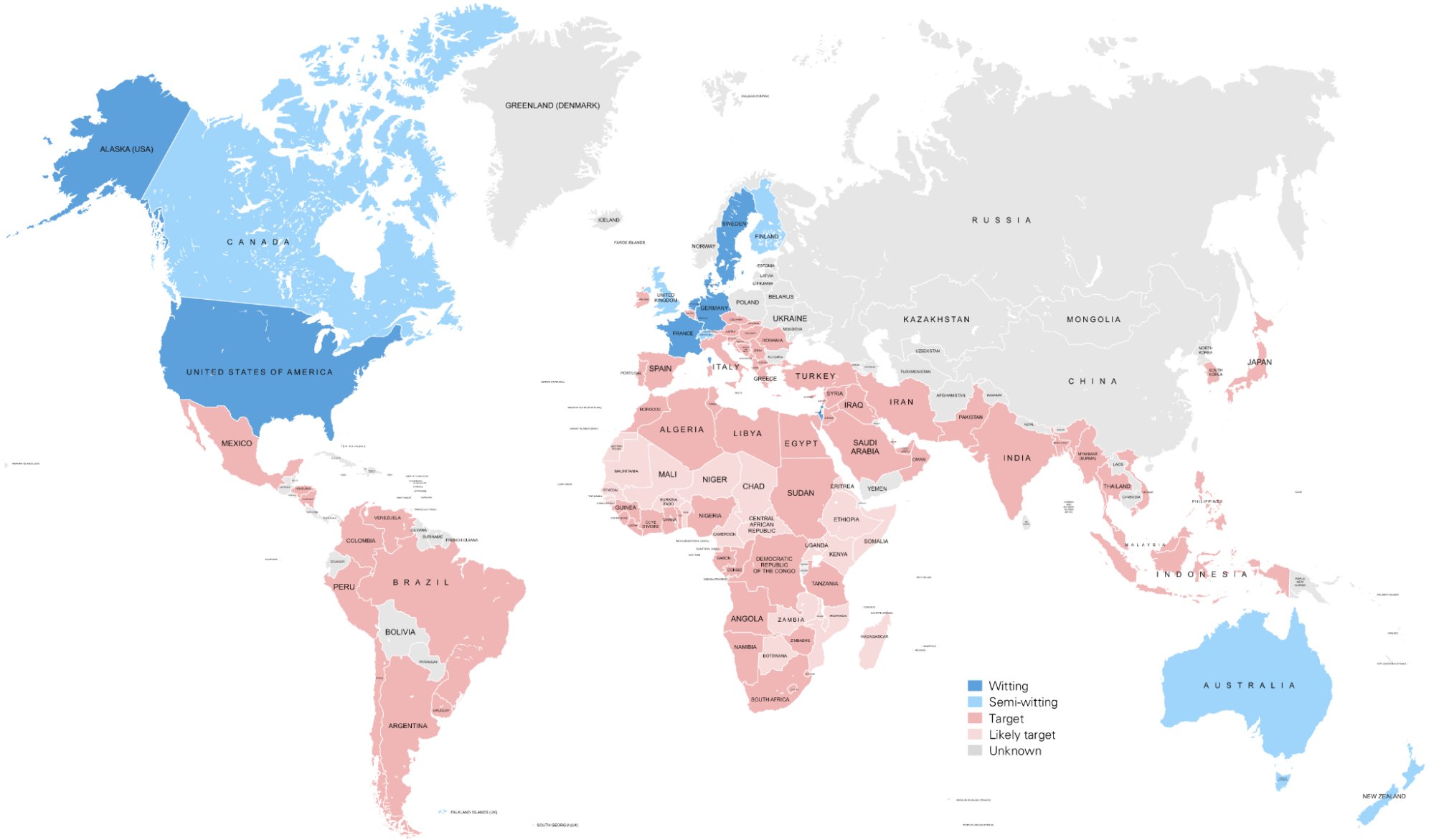
Across the next few decades, Crypto AG eavesdropped on the encrypted communications of more than 100 countries. Friend and foe alike effectively paid billions of dollars to have their state secrets read by the CIA.
Crypto AG machines were used by countries throughout S.America during Operation Condor, the two-decade US-backed program of violent political repression and assassination. The Pinochet regime in particular was instrumental in encouraging the Condor network to adopt the machines.
In 1991, Crypto AG’s immaculate reputation began to crack when news of the assassination of the sitting Iranian Prime Minister appeared to reach the US before the Iranians had even found his body. Iran quickly began to suspect their coms were compromised.
As a result, Iran arrested Crypto AG’s top salesman, Hans Buehler, during a sales trip to Iran on suspicion of spying. Unaware of the CIA/BND ownership, Buehler was interrogated for nine months and released after Crypto AG paid a million-dollar ransom.
Upon returning to Switzerland, Buehler was abruptly fired and ordered to repay the bond. Feeling betrayed, he began speaking to the press, joining other disgruntled former Crypto AG engineers who long suspected the company was controlled by Western intelligence agencies.
The resulting media coverage and court records drew significant attention toward ties between Crypto AG and the German & US intelligence services. Even though no hard evidence to substantiate the link would emerge until years later, the seeds of doubt had been planted.
From 1994 onward, Crypto AG was exclusively owned by the CIA. At its peak, the company had 230 employees and had offices in Offices in Switzerland, Ivory Coast, United Arab Emirates, Argentina, Malaysia, and Oman.
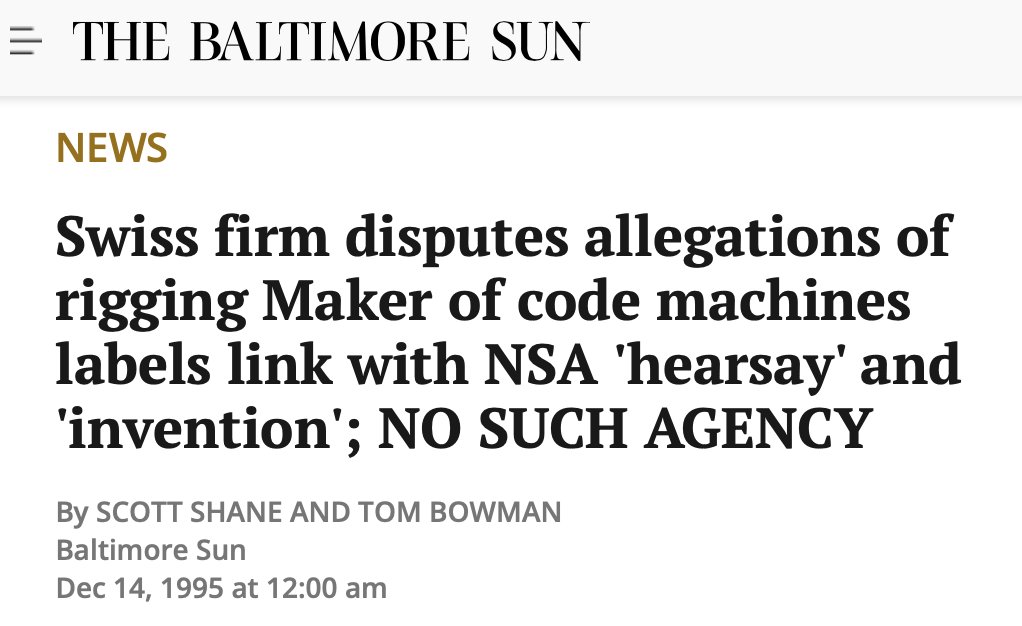
In 1995, the cover deteriorated further when journalist Scott Shane of the Baltimore Sun found clear indications of contacts between Crypto AG and the NSA dating back to the 1970s. The company responded, saying allegations of links were "pure invention."
A former Crypto AG employee found a 1975 memo showing NSA crypto mathematician Nora Mackebee had attended a design meeting. When Baltimore Sun journalists contacted Mackebee in 1995 to ask about Crypto AG, she went silent, responding, "I can't say anything about that."
In 2000, Covert Action Quarterly published an article outlining how Crypto AG had been an NSA trojan horse for the past 5 decades. But by this point, Crypto AG’s business had entered a terminal decline, eventually being unmasked entirely via a voluntary NSA document dump in 2015.
Through their deliberate manipulations, the CIA and BND eavesdropped on 148 countries for decades. Countries invested millions in Crypto AG’s rigged devices, believing that they were getting trustworthy technology from Switzerland when they were actually paying to be spied on.
Shortly before his death in 1983, Hagelin is said to have declared himself “the greatest spy of the 20th century”.
But two decades later, amongst the ashes of one of the most closely guarded secrets of the Cold War, an even greater tool of surveillance was born.
But two decades later, amongst the ashes of one of the most closely guarded secrets of the Cold War, an even greater tool of surveillance was born.
Part 2: