Thread
A few hours ago, a promising token called $YEAR was airdropped. It was set up as a "year in review" of your Ethereum transaction history.
Less than an hour ago, this turned into a painful experience for buyers of the token.
Here's how $YEAR pulled the rug in under 6 hours🧵 1/
Less than an hour ago, this turned into a painful experience for buyers of the token.
Here's how $YEAR pulled the rug in under 6 hours🧵 1/
EtherWrapped was a website which let you connect your Metamask wallet and view your year in history with ETH and ETH-based NFTs. It showed you the statistics of your wallet and calculated a token reward based on it. 2/
Everything in Ethereum is handled via Smart Contracts -- pieces of code that anyone may write and contribute to the Ethereum Virtual Machine (EVM) which you can consider to be a "world computer".
$YEAR is no different -- here is its contract: 3/
etherscan.io/address/0x9010a15184da16e3a7c5b4aa50094dfe3bb36989
$YEAR is no different -- here is its contract: 3/
etherscan.io/address/0x9010a15184da16e3a7c5b4aa50094dfe3bb36989
When you deploy a contract to the EVM, it starts out as an "unverified" contract to Etherscan which is the main source of truth for Ethereum.
Note: You should always be cautious of interacting with unverified contracts on the EVM. 4/
Note: You should always be cautious of interacting with unverified contracts on the EVM. 4/
After calls from members of the community, the creator of the $YEAR contract verified it.
This is important because a verified contract shares its source code with the world, giving us transparency into the code being executed whenever interacted with. 5/
This is important because a verified contract shares its source code with the world, giving us transparency into the code being executed whenever interacted with. 5/
At a first glance, this contract is really small. Myself and others looked over it and could not find any red flags.
The red flags we look for are:
- Can this contract drain your funds?
- Can this contract drain your NFTs?
- Can this contract do other malicious things?
6/
The red flags we look for are:
- Can this contract drain your funds?
- Can this contract drain your NFTs?
- Can this contract do other malicious things?
6/
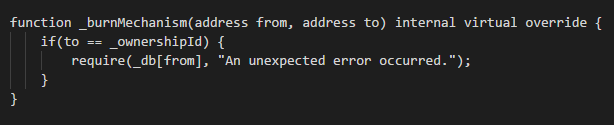
What we noticed during a brief pass was the presence of a function titled _burnMechanism.
This function looked innocent enough, it would fail if you attempted to interact with the contract owner.
What myself and others missed is how might one weaponize it for evil. 7/
This function looked innocent enough, it would fail if you attempted to interact with the contract owner.
What myself and others missed is how might one weaponize it for evil. 7/
Here's how it went down. At approximately 10pm PST, the creator of this contract called the `revokeOwnership` function of the contract and set its new owner to the Uniswap V2 contract address.
This effectively locked everyone out of being able to sell the token on Uniswap V2. 9/
This effectively locked everyone out of being able to sell the token on Uniswap V2. 9/
With this happening, the contract evolved into a honeypot where people could only make purchases but not any sort of sales.
This meant that on a DEX chart, people would see the candles going up only and induce FOMO to buy more before it spiked up further. 10/
This meant that on a DEX chart, people would see the candles going up only and induce FOMO to buy more before it spiked up further. 10/
Then, approximately thirty minutes into this honeypot, the creator went and took out liquidity from Uniswap V2 -- draining the pool of over 30 ETH across several transactions and zeroing out the coin. 11/
Here's what I've learned from the mess:
Bad actors know that their code can be audited quickly, and so they've resorted to hiding their exploits in plain sight.
We were all busy looking for an obvious red flag that we brushed over what looked like a novice coding mistake. 12/
Bad actors know that their code can be audited quickly, and so they've resorted to hiding their exploits in plain sight.
We were all busy looking for an obvious red flag that we brushed over what looked like a novice coding mistake. 12/
We also need to keep publishing postmortems like this.
In engineering culture, postmortems are designed to help each other get better after a failure.
They're also blameless -- everyone knows when they've messed up, the best thing we can do is help each other level up. 13/
In engineering culture, postmortems are designed to help each other get better after a failure.
They're also blameless -- everyone knows when they've messed up, the best thing we can do is help each other level up. 13/
I know we're all going to get better at spotting such bad actors moving forward.
The future of Web3 depends on it.
We're going to take what we've learned here and get better because of it.
The future of Web3 depends on it.
We're going to take what we've learned here and get better because of it.
One super super quick detail I forgot to add:
The _burnMechanism function was checked by the _transfer, _burn, and _mint functions of the contract.
_transfer is what happens internally as a step of a sell order and so it was preventing all sales to UniswapV2
The _burnMechanism function was checked by the _transfer, _burn, and _mint functions of the contract.
_transfer is what happens internally as a step of a sell order and so it was preventing all sales to UniswapV2