

A Look At the Lightning Network
Examining the scaling method of the Bitcoin network and its evolution from a store of value to a medium of exchange.


Recent decades have been characterized primarily by closed systems, both financially and online.
The financial system as we know it has been a rather closed system for ages, consisting of various silos. Banks and brokerages operate permissioned ledgers. Opening accounts with institutions is a permissioned activity. Sending assets between institutions is a permissioned activity domestically, and especially globally. The base currency itself has a central issuer.
The internet had many open aspects early on and still does, but it largely consolidated into silos over time. Twitter, Facebook, Youtube, LinkedIn, and platforms like these are closed networks. Opening accounts with them is a permissioned activity, how you use them is a permissioned activity, and sending information between these platforms has generally not been possible. How exactly do their algorithms work? Since most of them are closed, we can’t know.
Today, open monetary protocols (e.g. Bitcoin), as well as the emergence of newer open information protocols (e.g. Nostr), challenge this state of affairs and/or present alternative parallel systems for which people globally can use, explore, and build on. This article examines some of the prospects and potential implications of their adoption.
Bank accounts give users access to the traditional globally-connected banking system. A global network of interconnected banks allow for domestic and global money exchange, with varying amounts of settlement time for those transactions.
In recent decades, various fintech companies have developed as layers on top of traditional banking rails, to modernize and quicken the process of sending money. Contrary to popular perception, these types of companies aren’t going around banks or competing with banks; they are layers on top of the existing banking apparatus that still make use of various banks with central bank connections, but in a way that abstracts the experience for the user.
With credit cards, PayPal, Venmo, Zelle, and others- an increasing number of methods to move around small or medium amounts of money have greatly decreased digital payment times from the user perspective. Behind the scenes, however, there is still a complex and slow backend financial handshaking process that occurs along the way, as various intermediate financial institutions take on temporary credit.
In other words, when a small fintech payment seems instantly finished from the user perspective, the banks in the background are still spending hours or days finalizing it behind the curtain in larger batches, and thus holding IOUs to each other in the process.
Reliably sending global payments is much more burdensome, slow, and expensive. Wire transfers often get caught up and delayed in opaque ways. Many fintech services are only available in one economic bloc, such as the United States, and have no ability to send foreign payments. To the extent that a bank or service allows for global payments, it can feel like a stressful event each time, as you wonder if it will go through or get blocked for some arcane reason and need to be re-attempted, thus wasting time.
Buy automatically every day, week, or month, starting with as little as $10.
My local credit union used to offer international wire transfers (by piggybacking on Bank of America for the infrastructure, and for quite a hefty fee) but now no longer does. I have to use my Big Bank account now when sending global wires.
There’s an unfortunate problem for global payments: small transactions tend to have the highest percent fees, and their payees and recipients can least afford it. Many people in developing countries travel internationally for work and send money home to their families in small amounts, with intermediaries collecting high fees and not innovating quickly (or at all) to reduce them, and with little incentive to do so. According to the World Bank, the average fee percentage on a remittance payment is 6.3%. When sending remittance payments directly to banks, the fee percentage is 11.7%. Fintech companies and mobile payment solutions are responsible for lowering the average, but the average is still very high.
Globally, only about 76% of people have an account at a bank or at a fintech platform that connects to a bank. In many countries and regions, the numbers remain very low. In Nigeria, for example, only 45% of people have an account. In Palestine, only 34% do. Having a physical bank branch is expensive, and providing manual customer service comes with substantial overhead costs. If someone has a few hundred dollars, it is usually not worth the bank’s time to give them an account.
According to the World Bank, 75 countries also still have restrictions on women’s rights to manage assets. So, in addition to technical or monopoly-like problems with sending or holding money, there are some social bottlenecks as well.
Furthermore, many people aren’t aware of the problematic combination of refugees and banking. Banking is a centralized and permissioned activity, governed by a nation’s central bank, with tight regulation. This almost always involves mandating that the banks collect identification on customers. However, many refugees from impoverished or war-torn regions don’t have IDs and don’t have a clear or convenient path toward getting one, depending on the jurisdiction they’ve fled to. The problem is further compounded if they don’t have enough money or income for a bank to care.
Meanwhile, over 86% of people (over 7.1 billion people) have a smartphone globally, and the percentage is rising quickly. The proliferation and exponential nature of technology have allowed smartphone usage to leapfrog banking access in many areas. Phone and mobile internet adoption are expected to continue to spread into poorer and poorer areas over the next five and ten years.
People who work in what society considers to be undesirable industries often have trouble getting banked, or tend to get de-banked (including by fintech companies) after already being banked. Even the mere process of spreading information can lead to de-banking, such as the well-known case of Wikileaks losing its fintech payment platform access in 2010. If a protest is considered unacceptable, whether it’s in Nigeria or Canada or wherever else, protestors may have their bank accounts frozen, donations to protestors may be frozen or reversed, and even those making donations may find their financial access frozen.
And we must consider this from a global perspective: billions of people live in authoritarian countries and the number is not improving:
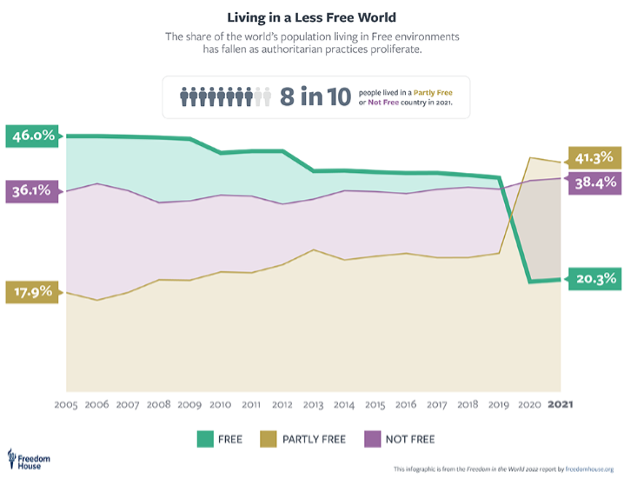
For decades since at least the early 1980s, cryptographers and cypherpunks researched ways to build internet-native monies that go around the banking system. Many early implementations were centralized, and thus either failed to accrue a network effect and stagnated into bankruptcy or were actively shut down by the government.
In 2009, Satoshi Nakamoto built on prior work and launched what has thus far been the most successful open-source monetary network: Bitcoin. For 14 years and counting, it has provided an open (yet still rather niche) payments and savings network to anyone with an internet connection, and in a way that has thus far been able to maintain decentralization and resistance to censorship. A subset of analysts around the world continue to examine it to determine 1) whether it will continue to exist and remain functional and 2) what implications it may have if it does.
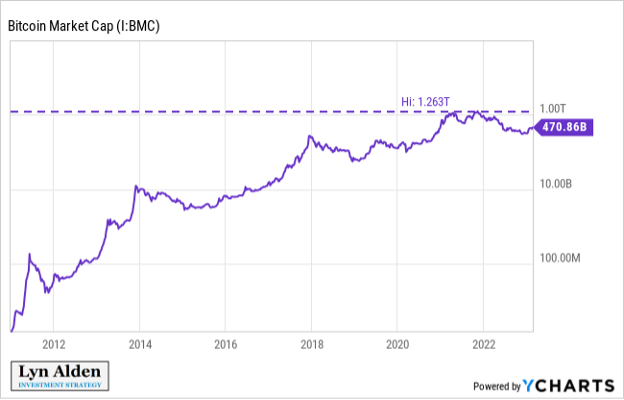
Nobody can reverse or censor transactions by decree; the only way to do so is to gain 51% of the network’s processing power and override the rest of the network. And since it’s an open-source network with nobody in charge, anyone with the physical capability to do so can interact with it in various ways:
A user can run a free open-source node client and participate in running the network, sending permissionless payments, and auditing details of the protocol.
Without even using software, a user can generate a private key by flipping a coin 256 times and use it to receive bitcoin as payments.
A user can memorize twelve words, travel across the world, and be able to reconstruct their ability to access their bitcoin at a later date.
A programmer can make a non-custodial wallet application that interfaces with the network and makes interacting with it easier for a non-technical user.
A financial services company can operate as a custodian, or as a collaborative custody provider that holds a 1-of-3 backup key in a multi-signature arrangement while the user holds 2-of-3 keys.
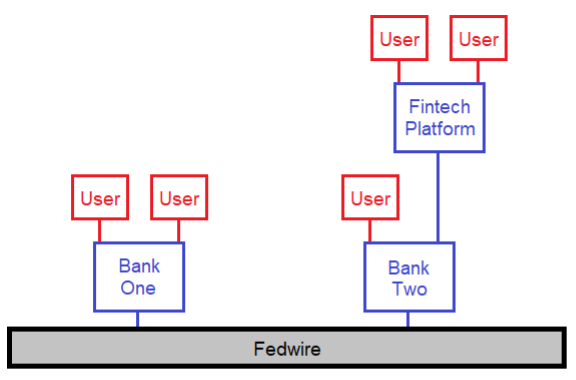
When we look at a closed monetary network such as the Federal Reserve system, it is strictly hierarchical. The underlying settlement networks, such as Fedwire, are only accessible to banks. To the extent that a user wants to make use of it, they can only do so indirectly, by being a customer at a bank or a fintech company that connects to a bank. To the extent that a fintech developer or a new bank figures out a way to make access to the network better, they can only do so with permission, by being granted access to a bank and following all regulations which vary by jurisdiction. The recent denial of Custodia Bank’s application is a recent example to show how permissioned and hierarchical the system is.
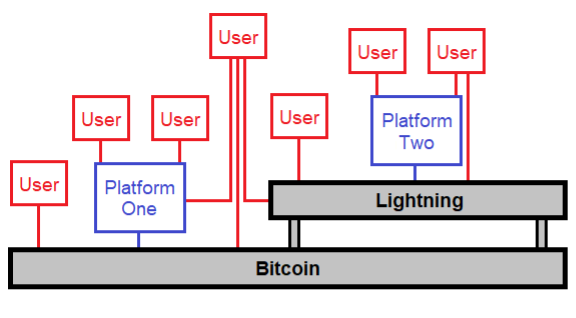
An open monetary network works differently. Users can directly access the network if they want to. Or they can go through larger platforms that make various trade-offs for the sake of convenience. Furthermore, people can directly interact with whatever part of the stack that suits their specific needs at a specific time, such as the base layer or software layers on top of it (e.g. Lightning). Any developer can create a new way to interface with it, or a new layer on top of it, and offer it into the global marketplace without waiting for an application to a centralized authority to be approved.
On its surface, the internet seems reasonably decentralized. A consistent protocol stack built around Internet Protocol is used around the world, and on top of that protocol stack there are various websites or other types of servers, and there are multiple different methods to access them (e.g. different operating systems, browser applications, and so forth).
The way that people tend to use it, however, has become quite controllable and siloed. The rise of major social media platforms like Facebook, Youtube, Twitter, LinkedIn, and others consolidated many users into big pools of connectivity. Rather than everyone making their own websites, most users create accounts on big platforms and thus subject themselves to the various rules and algorithms of that platform in exchange for the convenience and access that those platforms provide. Billions of people congregate around these pools of activity, which are offered for free in exchange for harvesting all of their data. Small and separately-run internet forum websites used to be popular, but these have tended to consolidate towards subsections of major social media platforms. To the extent that people search for new websites, it’s dominated by Google’s search algorithm.
A Twitter user can’t send a direct message to a Facebook user. A LinkedIn user can’t bring their followers with them if they create a Twitter account. They all tend to be siloed.
Those platforms then use various private algorithms to determine what information gets shown to users and have discretion around content moderation policies to remove posts or entire accounts as they deem fit, or as required by their government.
We can imagine this from a corporate, government, and user perspective, and see what each one is trying to maximize for.
From a corporation’s perspective, they need to be able to remove illegal activity or outright spam, so that they can comply with laws and so that their platform doesn’t turn into a tragedy of the commons. They also need to tune their algorithm in such a way that it gives people the connections that make sense to them and keep them on the platform rather than going elsewhere.
From a government’s perspective, people act very differently online than offline. They are more impersonal, more aggressive, and easier to manipulate with fake data (including via foreign agents) when online. Algorithms, if improperly tuned, can feed a billion people more of what makes them emotional from people who are already in their digital tribe, and thus close them off from each other and repeatedly exaggerate public outrage in recurring waves.
From a user’s perspective, government and corporate power over moderation is prone to corruption. A government can demand a takedown of information that is inconvenient to them or that doesn’t fit their preferred narrative. Corporations can exacerbate outrage and user emotions if it translates into more dollars at the end of the day. Much like the military-industrial complex that has been around for decades, there is a political-finance-media complex as well.
India, as a very large but relatively mild example, has established a track record of telling Twitter, YouTube, and other platforms to remove information that is unfavorable to their current administration, and those platforms comply. In many countries that are more restrictive, social media platforms are completely controlled or banned, leaving their population in the dark and disconnected from the rest of the world.
Even private messages can be read by those in power. Some platforms use unencrypted direct messages. Other platforms claim to use encrypted direct messages, but there is no way for a user to prove that they really are encrypted. Unencrypted messages can be read by insiders at the corporation, by government agents requesting such information, or by hackers that can and often do get illegal access to them.
A user cannot audit the way that a platform’s closed-source algorithm works. A Facebook user cannot send a direct message to a Twitter user. If an account is frozen or removed, a user can appeal but otherwise has no recourse. If social media is not allowed in a country, people have their information and connectivity greatly reduced and controlled by centralized forces.
People have been trying to make more decentralized internet and social media experiences for a while, but it’s hard to compete with the network effects that the big centralized ones have established. A centralized server tends to be very efficient and self-reinforcing, and so centralized solutions get deployed, get the initial users, and thus entrench themselves for decades.
One of the ways to decentralize the internet is to normalize running a home server and make it easier to do so. As technology improves, basic server-grade computers have become more accessible, and a number of hardware and software solutions have come into existence that is geared toward a consumer server market. However, there are still long-term limitations on peoples' interest or financial ability to run a server. The financial and bandwidth constraints are particularly problematic for potential users in developing countries.
On the other hand, some technologies enable more peer-to-peer information transfer. File-sharing, video calls, and things like that can allow people to connect to each other in high-bandwidth ways. Keet, for example, is far faster and higher resolution than Zoom for video chats involving modest amounts of people. A challenge with pure peer-to-peer models is that both users have to be online at the same time to coordinate.
A middle-ground method that seems to be beginning to work at scale is the idea of distributed servers or “relays”. In this model, not every user has to run a server, but individual servers are relatively easy to run, are financially incentivized to be run, and are therefore numerous enough that there is no way to control or censor the network. The result is a rather decentralized web of servers that connect to each other, and users that connect to them.
A good example of this is Nostr. It’s an open-source protocol that stands for “Notes and Other Stuff Transmitted by Relays”. For the first two years of its existence, it was relatively unused, but in 2022 it started to get more traction. By the end of the year and into early 2023, thanks to efforts by Jack Dorsey and others, it started to gain some serious adoption.
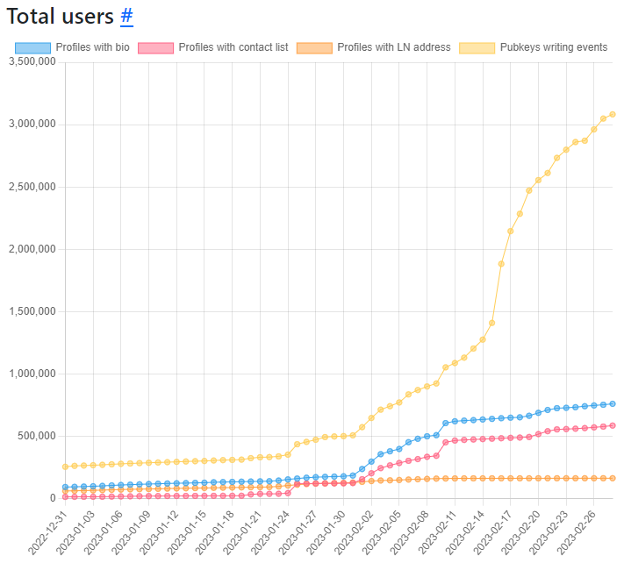
Nostr Band
On top of Nostr, anyone can build a client application for it. Users of different clients can see each others' posts and send messages to each other. A person can use different clients over time and still have access to their followers. One client might look kind of like Twitter. Another client might look kind of like Telegram. So far, clients that look like Twitter have been the preferred client type.
The closest analogy is perhaps to compare it to email. People who use Gmail, Yahoo, Hotmail, AOL, and various individual webmail services, can all send emails to each other regardless of which service they use. This is because they are all built on the same underlying set of protocols, and are not closed/siloed systems.
Similarly, Nostr is an underlying open-source social media publishing protocol that people can build clients for. People have made Twitter-clone clients, Telegram-clone clients, desktop clients, and mobile clients for Nostr, and they are all compatible with each other.
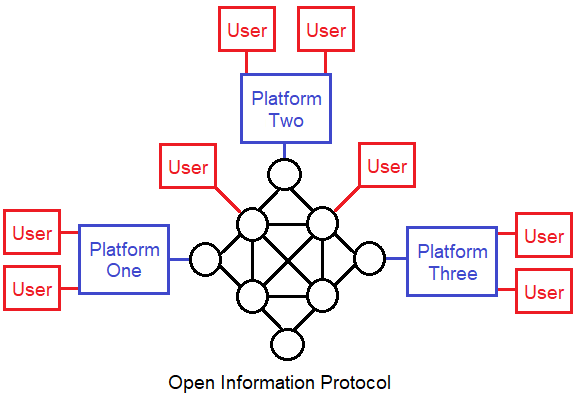
A nice attribute of this model is that if someone has a really good idea for a new type of social media platform, they don’t have to worry about network effects. They can create a new experience, meaning a new client interface, connect it right into the Nostr protocol, and make it interoperable right from the start with every other Nostr user across existing clients. They can make use of the existing network effect, in a similar way that any new browser or new email provider makes use of the extensive network effect that already exists for those protocols.
And it can extend beyond social media. Jack Dorsey has stressed this idea and pointed out for example that it could be used as a GitHub replacement. The anonymous computer scientist and author Gigi has referred to it as an “identity and reputation layer”. Willy Woo described it as everything Twitter wanted in its early years with an open API. Elizabeth Stark, CEO of Lightning Labs, pointed beyond Twitter clones and wrote that “an open messaging protocol means you can build things that weren’t previously possible in the old walled garden centralized paradigm”.
To use Nostr, you generate a private and public key pair in one of multiple ways. Most clients can do this for you, and third-party applications like Alby can do this for you. You keep the private key secret, and the public key is like your username that you share with other people.
There is no central server (or “relay”), and instead, many individual users run relays. Users can pick which relays they connect to, and relay operators can ban certain users from their relay. Users publish material to multiple relays, and relays transmit and store that material, with discretion by relay operators about which material they choose to transmit and store on their particular relay.
Nostr makes native use of the Bitcoin/Lightning network, without being built on it. Users can easily tip each other with Lightning transactions or pay premium relay operators with Lightning payments in order to use those relays instead of the various free ones. Other paid services can be offered over Nostr as well.
The combination of public-key cryptography and distributed servers means that no central entity can censor anyone or ban anyone from the protocol, in a similar way that nobody can be “banned from email”. A government can target and shut down individual relays in their jurisdictions, but there could be quite a number of them, and individuals around the world can run relays, and users can connect to relays in other jurisdictions. Individual relay operators can choose to exclude things, and if users want to exclude certain things they can stick with those more exclusive relays. Some relays can operate for free and other ones can charge a small fee. Different client applications can configure different settings or appearances, and users can determine which clients to use, and use multiple different clients.
It also means that some of the user experience is a bit clunky at the moment. If a user doesn’t connect to good relays, the speed will be slow and some data will be incomplete, like seeing posts but being unable to see the posts that they are in response to. It’s not easy to track how many followers you precisely have, or how many likes a particular post really gets. Users have to be careful about which clients to trust- if you insert your private key into a scammy client, they can use it to capture your protocol-wide Nostr digital identity. The bandwidth usage in practice is rather high, particularly for developing country internet infrastructure- there has been a priority on making things work more than making things efficient.
I expect that some of the clunky aspects will be smoothed out over time; at the moment the ecosystem is basically devoid of capital with a handful of people working on it, and yet it’s already quite impressive as it is. It looks like a powerful set of individual building blocks coming together. It’s really early.
Even the bearish case for this technology is to say that it is something that will exist now but remain niche, and thus is a new tool that is usable by the people that need it.
For many years now there has been a fad around the concept of “blockchain technology” as it relates to decentralization.
Some of the big themes have been along these lines:
Internet-Native Money
Asset Tokenization
Decentralized Media
Digital Identity
All of those things, indeed, are important avenues of research. Bitcoin is a useful internet-native money. Stablecoins tokenize the dollar and make it more accessible to people around the world. Decentralized information protocols can give more people access to information and connections without centralized moderation or a centralized server to shut down. Digital identity gives someone the ability to prove themselves to be a continuous entity across different digital platforms and across time.
However, in recent years, the idea of “Web3” has been used mainly as a marketing tool for the third and fourth items on that list. Anything with “decentralized” or “blockchain” as part of its claim has tended to get a lot of capital. Venture capital firms can deploy capital into a token project, pump up a lot of hype for it, encourage users to come into its ecosystem with ponzi-like financial characteristics, sell their tokens to retail investors after a couple of years, and walk away with big gains regardless of the fact that the project had no long-term staying power.
In such an environment, user metrics are distorted due to there being so many financial incentives that are not necessarily in line with using the software for its own sake. The joke, therefore, is that “Web3 has more investors than users”. And the level of decentralization is often overstated as part of the marketing effort.
A big issue here is that most platforms simply don’t need tokens, don’t benefit from tokens, and are made worse by having tokens.
Sure, existing securities or assets can be tokenized, and that can be useful. Tokenized dollars, tokenized stocks, tokenized receipts for things, etc. These are centralized assets, but their peer side is expanded into a bearer asset and tradeable globally by anyone with a smartphone. That’s a real use-case to people, although it does come with regulatory risks and counterparty risks.
But many decentralized things, and particularly platforms, are stronger without a token. The purpose of a token is often to enrich a smaller number of early creators or investors rather than to enhance the actual product or solve an actual problem. The existence of a token is often unnecessary and deleterious to a project. It’s often just a method of regulatory arbitrage to go around existing securities laws.
Along these lines, way more things are advertised as benefiting from a blockchain than really do. A blockchain helps different entities come to a global consensus on something, and that’s an expensive process that only needs to be applied to things that truly need it.
An example of something that truly needs global consensus is a shared global ledger, such as Bitcoin. In order to audit the supply of the Bitcoin network and validate all transactions, nodes need to agree on the full state of the ledger, globally and continuously. A blockchain solves this.
Bitcoin is like a big decentralized spreadsheet that the world comes to an agreement on every ten minutes, using energy from miners and the rules enforced by the user-run node network as its arbiters of truth. This is an expensive process, but a valuable one that isn’t solved by other means.
Next down the line is tokenized assets, such a stablecoins. The centralized issuer needs to know how many claims for their assets exist, and likely needs to be able to freeze individual ones and re-issue them as needed. On the other side, the user needs to be able to prove their claims of ownership to the issuer. It’s less critical (but potentially still desirable) for a user to be able to cheaply audit the entire supply of other user claims, since they are relying on a centralized issuer anyway.
And then, issuers and users need composability: pieces need to be able to interact in many different ways relatively seamlessly for the ecosystem to be notably superior to the existing financial ecosystem. This gives users considerable flexibility over how they hold an asset, where they trade it, whether and where they leverage it as collateral, and so forth.
So far, this type of activity has benefited from a blockchain and a global consensus, although there are research efforts that suggest other avenues may exist. These can be thought of as methods to improve the tech wrapper for existing security issuers, exchanges, collectibles, liquidity/leverage services, and fiat payment services.
From there, we get into decentralized communication and social media and see that global consensus is not needed or even desirable.
We don’t come to a global consensus on “all emails” for example. Email providers make use of global protocols and yet there is no entity that needs to or has the technical capability to catalogue the current state of all emails globally. In fact, it would be a problem for privacy if they could.
Similarly, Nostr doesn’t require a global consensus and thus is not a blockchain. Relays don’t need to all communicate with each other and ensure they all agree. Users don’t need to connect to every relay. The network is open source and interoperable, and users can figure out how much of the network they want to see based on how many relays they want to connect with, and how many people they want to follow.
Attempts to use a blockchain as an underlying technology for social media or similar types of internet experiences don’t make sense in my view, because the cost of coming to a global consensus is expensive, doesn’t necessarily add to the experience, and may detract from the experience.
Lastly, digital identity also does not require global consensus.
The existence of a public/private key pair, for example, can be used to prove continuous identity (or at least continual ownership of the private key) across platforms and across time. Similarly, organizations or applications can provide more comprehensive identification services, and give the user the ability to selectively share part of that information with approved receivers of that information. Some of these applications may make use of a blockchain or a layer built on one.
There need not be a global consensus of all identities, nor would it necessarily be desirable if there were.
I transferred some Bitcoin from one of my old crypto exchange accounts to a mobile lightning wallet a while ago.
If I was in a developing country, even one where the banks don’t let me send money out to bitcoin brokerages or crypto exchanges, I could have earned the sats via Stakwork instead (Stakwork is a platform that, using the Lightning network, connects people who want microtasks done, to people able to do microtasks globally). Or, I could have acquired some with physical cash via Azteco, a voucher system.
I tend to play around with different wallets for research purposes, so I have both custodial and non-custodial varieties. One exercise I did to test different user interfaces is to quickly send some fractional bitcoin (commonly referred to as “sats”) from wallet to wallet on my own phone. Each transaction would take about three seconds. Bearer assets were jumping from custodial wallet to noncustodial wallet to custodial wallet to noncustodial wallet. Fees were a fraction of a penny, and the process was automated and within my control. I’ve also helped people download a wallet and send them some sats in a couple of minutes.
From there, I transferred some sats to my Stacker News wallet, which took about three seconds. Stacker News is a Reddit-like website that requires paying sats to post, which helps prevent spam but is not actually expensive for human users. Users can tip each other with sats, and thus posting good content can earn you some sats. I transferred sats over to there so that I could post, and ended up receiving a bunch of tips on my posts.
Recently, when trying out Nostr, I did something similar. I installed the Alby plugin on my browser, and used it to create a new wallet. I transferred some of my Stacker News sats over to my Alby wallet, which took about three seconds. On my Nostr client, I listed my Alby wallet there. From that point, users could easily tip me some sats to my Alby wallet. I of course tipped some other people as well and could pay for access to a premium relay. At any time, I can pull sats out of these ecosystems and into deeper cold storage; these custodial and noncustodial lightning wallets can be thought of as like cash in a wallet, with similar trade-offs as it relates to convenience and security.
The combination of an open monetary network and an open information network is pretty interesting. Programmable bearer asset money can move around frictionlessly across borders, and between platforms. Platforms can be interoperable with each other without directly working with each other to make it happen, simply because they are interfacing with the same underlying protocols. Server operators can be incentivized to maintain and enhance an information network via microtransactions.
A set of protocols that globally connect people in terms of identity, information, and value can reduce a lot of frictions and create a lot of new opportunities.
Open commerce requires the transfer of both information and value. Therefore, both open monetary networks and open information networks (and their actual usage rather than merely their existence) matter for the study of economics, geopolitics, and various long-range investment outcomes.
In general, any jurisdiction that is attractive in the sense that people and capital want to come to it, and information can be shared freely within it and with the rest of the world, should welcome such technologies. Open monetary and information networks, especially if their usage spreads around the world in ways that are hard to prevent, enable and accelerate more value flowing into these freer jurisdictions from elsewhere. Borders become less relevant from an economic point of view.
On the other hand, any jurisdiction that is unattractive in the sense that people and capital want to escape it, and information is restricted within it and with the rest of the world in order to protect the rulers, should fear such technologies. Open monetary and information networks create more leaks of capital and information into and out of their jurisdictions, empowering their people, or forcing more expenditure by their rulers to increase the existing restrictions to maintain their isolation.
In older days, when the exchange of cash or coin was more commonplace, transactional privacy was the default. As the world consolidated onto bank ledgers, however, privacy began to go away.
The 1970 Bank Secrecy Act, enacted into law by the U.S. government and still in effect, compels banks to file reports with the government if a customer’s daily transactions exceed $10,000.
When this law was enacted in 1970, the median American annual income was less than $10,000. So, the law only covered rather large sums of money moving within a day, worth well over $80,000 in today’s weaker dollars. However, there was no inflation adjustment embedded into the law. As the value of the dollar eroded over time, banks effectively had to file reports regarding smaller and smaller levels of transactions, since $10,000 worth of transactions occurring in a day became more and more commonplace. Every year, the government effectively lowers the threshold regarding its automatic financial surveillance, simply through inflation, without passing further legislation.
Over the next fifty years, if the rate of inflation averages the same amount as it has over the past fifty years, then the reporting threshold will shrink by another 8x or so in terms of purchasing power. When the law was enacted, the government granted itself the ability to keep tabs on house-sized transactions. Over time, inflation enhanced the law so that they can keep track of transactions the size of used cars. If this keeps up, it will enable them to keep track of transactions the size of lawnmowers or bicycles.
This is an example of expanding a surveillance mandate continuously, without having to pass new legislation to do so. Inflation serves as the ever-expanding mandate.
Of course, with other technologies and surveillance methods, or with court orders, or with new legislation, authorities can already see any-sized bank transaction that they want as well.
Privacy in communication, movement, and other aspects of life used to be expensive to violate. Prior to the widespread usage of the internet, smartphones, surveillance cameras, and other technologies, the only way to violate someone’s privacy was to physically spy on them, search their person, or search their property. And for this reason, the person who had their privacy violated had a good chance of knowing that it was violated.
In the digital age, it’s increasingly easy and inexpensive for governments, corporations, or individuals to violate someone’s privacy, and without that person knowing. For governments and corporations, a combination of public and private information on millions of people can be harvested automatically on all of the major digital platforms and portals. That data, once collected, can be organized by various Big Data techniques including machine learning, and then algorithmically monitored or made easily searchable to users of the database.
In 2013, a U.S. National Security Agency contractor named Edward Snowden leaked information to journalists that revealed that the U.S. National Security Agency’s surveillance capabilities extended far beyond what was previously known to the public. Specifically, the NSA was revealed to be able to directly tap into the systems of major telecommunications providers and large corporate software platforms to continually harvest information.
In one of the original reports on the leak, the Guardian revealed:
“The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple, and other US internet giants, according to a top-secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called Prism, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says.”
As our lives become increasingly digital, it has become easier for our information to be harvested by corporations and governments. Privacy can be violated automatically, at scale, inexpensively, and without the user knowing.
In Western democracies, this has downsides but has so far been generally unfelt by the domestic population. Most of the human rights violations committed by developed countries these days tend to be international, either from colonialism in the past or from neocolonialism in the present. In authoritarian regimes, however, the consequences are more domestic. People can be arrested for criticizing their government. People can be executed for being homosexual. People can be put into camps for having a minority religion.
Last year, a young Saudi woman and mother of two children, who was a student at Leeds University in the UK, was arrested when she returned home to Saudi Arabia and sentenced to 34 years in prison. Her crime was that she followed and retweeted various activists on Twitter, while she was in the U.K. A couple of months later, a 72-year-old Saudi-American dual citizen living in the United States was arrested and sentenced to 16 years in prison when he returned to Saudi Arabia for what was supposed to be a brief trip. His crime was that he tweeted critically about the Saudi regime while in the United States.
This also happens to people in countries that are popular tourist destinations. People have been given 25-year prison sentences in Thailand for posting pictures online that are deemed insulting to the country’s monarchy. Ahmed Monsoor was sentenced to prison for a decade for advocating for human rights in the UAE in a way that was critical of the rulers. As Human Rights Watch reported:
At his third hearing, the judge read out six charges against Mansoor, all entirely based on his human rights activism and advocacy. The court later convicted him of five of those charges, all based on simple acts of human rights advocacy, including tweeting about injustices, participating in international human rights conferences online, and (since deleted) email exchanges and WhatsApp conversations with representatives of human rights organizations, including Human Rights Watch and the Gulf Centre for Human Rights (GCHR). The court acquitted him of the sixth charge, “cooperating with a terrorist organization.”
The court based its verdict, announced during the fifth and final hearing, on the penal code and the 2012 cybercrimes law, both of which make the peaceful expression of critical views of the authorities, senior officials, the judiciary, and even public policy a criminal offense and provide a legal basis to prosecute and jail people who argue for political reform or organize unlicensed demonstrations.
Over 1.4 billion people have information suppressed in China and are subject to varying levels of authoritarianism. India, another country of 1.4 billion people is much less restrictive, but still gets information removed from social media and has a mixed human rights track record. Hundreds of millions of people across parts of the Middle East and parts of Southeast Asia are subject to authoritarian rule. Vladimir Putin’s political opposition, Alexei Navalny, was poisoned, and upon surviving and returning to Russia, was put in prison and remains there until this day. A subset of Latin American countries and African countries have an authoritarian rule. It’s an extremely widespread problem. Meanwhile, institutions that are largely run by developed countries, such as the IMF, gladly work with authoritarian regimes, which can help keep them in power.
One of the defenses that people have against authoritarianism is private, encrypted communication and information. This allows for the transfer of information and value, including in private ways. Technologies such as this will rarely be provided in a top-down way; instead, if they are to exist and be resilient, they must be built in a bottom-up and highly distributed way.
Along the way, such technologies will be painted as tools of drug traffickers, sex traffickers, and terrorists by those who are in power. And what will complicate matters is that yes, just like pagers, just like the internet, and just like any powerful technology or network, criminals will be among those that use such tools. And yet, those tools are necessary and can help far more people than they can hurt.
Authoritarian regimes have often turned to obvious anti-privacy techniques in order to prevent revolutions. Such regimes want to control the spread of information as much as possible.
In Western democracies, anti-privacy crackdowns have instead been more gradual, and have generally existed on the institutional level rather than the consumer level. It’s easier to get several thousand highly-regulated banks and a few dozen major internet platforms and telecommunication companies to comply with continuous financial and information surveillance than it is to get hundreds of millions of individuals to do so.
We generally have a rolling set of reasons for why privacy needs to be violated in such a continuous, systemic, and automated way. Throughout the 1970s, 1980s, and 1990s, it was often argued that financial and information privacy must be restricted in order to restrain drug trafficking. Back in the 1980s, for example, pagers were a source of consternation:
“Although paging devices, or beepers, have grown in popularity throughout the labor force — doctors, delivery people, and journalists often use them — they also have become a staple in the drug business, posing fresh problems for law enforcement and threatening to tarnish the image of a booming high-tech industry.”
— Washington Post, 1988, "Message is Out on Beepers"
Starting in the 2000s, it was terrorism financing that took center stage instead. The 2001 Patriot Act, among other things, expanded surveillance capabilities by the U.S. government in the name of fighting terrorism. The NSA’s programs in the 2010s, revealed by Snowden, further expanded and automated that capability by connecting with major internet messaging platforms and aggregating as much online communication as possible.
More recently, the public messaging around restrictions on privacy has been about child imagery and/or sanctioned nation-states. Throughout 2022, the European Commission proposed legislation that would try to eliminate all private communications by mandating the automatic scanning of emails and messages, including encrypted messages, for certain types of illegal content. While everyone is of course against the existence and distribution of such dreadful imagery, the idea that every communication method of all citizens must be continuously scanned and made accessible to the government is argued by many to be an extreme overreach. Similarly, the U.S. Treasury sanctioning of Tornado Cash was a crackdown on cryptographic privacy methods due to its association with DeFi hacks, including by North Korea. Any entity that handles funds on a commercial scale has done various identity checks, and so various centralized private custodians tend to be regularly shut down. In the modern era, unlike in the past, financial privacy is considered to be synonymous with money laundering.
Another problem relates to tax collection. Back in older times when transactions were more inherently private, something like an income tax was relatively unworkable. Taxes tended to be placed on property and on exports/imports, and on income for large establishments or estates because all of that was quite visible and auditable. In contrast, taxing income at the individual level was generally a messy proposition due to the difficulty and expense of auditing it. Even today, accurately taxing cash-dominated businesses remains a challenge.
However, with the widespread conversion towards bank ledgers and automatic employer paychecks, it became easier for governments to audit incomes and to tax them. Employers pay their employees, report the payouts to the government, and the whole process is auditable. Income taxes thus became a dominant form of taxation.
Going forward, if a meaningful portion of the economy shifts towards peer-to-peer global gig work, and money and information in general become more encrypted and private, and money is able to be self-custodied and moved around globally, then what does that mean for governments' ability to audit incomes and impose taxation on those incomes at the individual level? Such auditing and assessment could become much more expensive, and for sophisticated users, potentially becomes impossible.
One perspective would be that governments simply have to change their patterns of taxation over time, if indeed bottom-up open-source distributed privacy technology and open monetary/information networks become more widespread. In some sense, this would be a return to how things used to be, except in the digital realm. A greater portion of taxation would have to be on more physical, large, and visible things, such as property, major enterprise, and the logistics and sale points of physical products.
The other perspective, generally from the viewpoint of the government, is that instead, all privacy has to be eliminated, then. Every transaction between every peer, globally, has to be monitorable so that it can be audited and taxed. Even if an open-source bottom-up emergent technology is developed to enable privacy, such technology must be outlawed and/or marginalized as much as possible to prevent its widespread use. It may even be necessary to place more restrictions on the developers of such technology, as the Digital Asset Anti-Money Laundering Act essentially proposed.
Unfortunately, this second perspective takes on a very different meaning when we remember that billions of people live under authoritarianism and that people can readily be arrested and sentenced to long prison terms for criticizing their government, organizing protests, having the wrong sexual orientation, having the wrong religion, or otherwise having some minority or disapproved aspect of their life.
Over the long run, I view the outcome, one way or the other, more as a matter of technology than politics. From the top-down side, there is the development of Big Data and automated data surveillance capabilities. From the bottom-up side, there is the development of encryption tools and open monetary/information networks. Whichever direction proves more powerful will play a major role in how all sorts of things operate in the decades ahead, including various economic interactions.
Therefore, for proponents of privacy and open networks to win becomes a matter of making the technology easy to use, too costly to stamp out, and well-understood by the public. For proponents of ubiquitous surveillance to win becomes a matter of convincing the public that privacy is undesirable and that these tools are not needed or are dangerous while enhancing their data collection and sorting capabilities.
And from an analyst perspective, the challenge and the opportunity is to see where these trends are headed, which means monitoring the progress of both the bottom-up and the top-down approaches to see who is in the lead.
Editor’s Note: Have you created a Swan account yet? Join Lyn Alden and start stacking sats with us.
Head to Swan.com/alden you’ll get $10 in FREE Bitcoin after you create a swan account.

Lyn is an investment strategist at Lyn Alden Investment Strategy. She holds bachelor’s degree in electrical engineering and a master’s degree in engineering management, with a focus on engineering economics and financial modeling. Lyn has been performing investment research for over fifteen years in various public and private capacities.
News
More NewsThoughts on Bitcoin from the Swan team and friends.



By Lyn Alden
Examining the scaling method of the Bitcoin network and its evolution from a store of value to a medium of exchange.



By Yan Pritzker
Swan Guard brings world-class Bitcoin security with advanced risk controls, scam defense, and expert support — vigilantly protecting your Swan account and safeguarding your Bitcoin.



By Alex Stanczyk
After managing a Swiss gold fund for 8 years, I realized Bitcoin surpasses gold as the ultimate store of value. Here’s why every gold investor should study Bitcoin closely.